GMV adapts ATMs to the maximum security levels of the future

GMV was present at BankSec, the online event organized by Retail Banking Research (RBR) to analyze the characteristics of ATM cyberattacks and recommended the best protection measures against them. It has to be borne firmly in mind here that ATM network protection strategies in each case will depend on the real and perceived threats faced in each part of the world. It is also essential for these protection measures to be continually tweaked and updated as new attacks and operations develop, always striking the right balance between ATM protection and customer convenience.
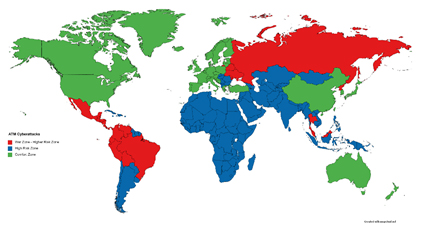 The map shows the graded worldwide ATM cyberattack risk. The red zone, identified as a “War Zone”, corresponds to countries that have reported the biggest number of attacks and where organized criminal groups are most active. These countries have the highest risk awareness, faced as they are with almost daily occurrence; they have therefore rolled out the highest number of ATM protection measures. At the other end of the scale come the countries in the “Comfort Zone”, where the sensation of risk is lower, the rollout of protection measures slower and, in many cases, insufficient.
The map shows the graded worldwide ATM cyberattack risk. The red zone, identified as a “War Zone”, corresponds to countries that have reported the biggest number of attacks and where organized criminal groups are most active. These countries have the highest risk awareness, faced as they are with almost daily occurrence; they have therefore rolled out the highest number of ATM protection measures. At the other end of the scale come the countries in the “Comfort Zone”, where the sensation of risk is lower, the rollout of protection measures slower and, in many cases, insufficient.
The sheer sophistication of attacks in the War Zone” has forced banks to deploy security policies and protection measures that can come up with the quickest response to these attacks. The good practices adopted by these banks should be the baseline for the rest of the banks, especially those located in the “Comfort Zone” and, in general, where protection measures have been found wanting, bringing them up to the level found in the more severely affected areas.
An analysis of the most recent attacks shows that most of the exploited vulnerabilities stem from the use of backdoors by the banks themselves to make their ATMs more user-friendly. For example, the possibility of connecting USBs to ATMs is a weak point that many banks tolerate to enable their technicians to carry out on-site maintenance work.
If we now turn our attention to the ATM networks, we could perhaps define their hallmark trait as stability: stability of the software, of data, transactions and execution in general. We also know that attacks tend to shake up this stability like an earthquake: incomplete transactions, skewed execution sequences, abnormally high or low amounts, etc.
These inherent ATM traits mean that behavior-analysis and anomaly-detection technology really comes into its own here. This needs to be based on a stable and well-known system behavior without suffering any upsets caused by vendor- or model-heterogeneity of the ATM networks. The XFS layer provides this desired stability and uniformity, cancelling out the vendor or model idiosyncrasies while also ensuring direct access to the ATM’s most critical and basic functions. This layer also allows for a complete and very dependable analysis of ATM behavior, flagging up the slightest anomaly and cutting down the number of false positives.
In many cases, however, the detection of anomalies is not enough to fend off an attack; it needs to be rounded out with measures to block off these anomalies. Once more, the XFS layer constitutes the perfect input point not only for analyzing behavior but also detecting anomalies, taking the necessary measures to ward off this suspicious behavior.
We at GMV have developed a new ATM security product, Checker XFS Filtering. At ATM XFS-level it implements a complete ATM-security solution, combining ATM behavior analysis, anomaly detection and filtering of suspicious actions. This new GMV solution is a natural upgrade of its longstanding ATM-security product, Checker ATM Security, to ensure the maximum levels of security.